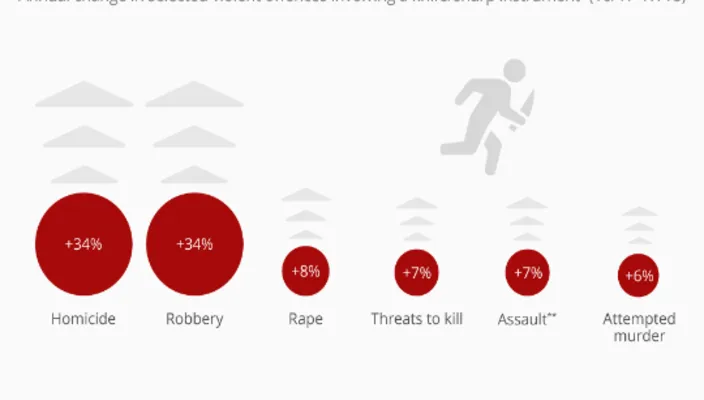
Knife crime on the rise in the UK In addition to disrupting its C2 infrastructure, the operation also closed the external management ports that the threat actor used to establish connections with the firewall appliances, effectively severing contact and preventing the hacking group from using the infected devices to commandeer the botnet.
↑
Copyright © Earnflex 2026, All Rights Reserved. V 26.01.26 Website Reload